Link Layers Newsletter
Another Layer of Protection Added to Our Stack
We’re excited to share an update to our managed IT services—one that strengthens our ability to protect, support, and simplify your technology environment. We’ve added a new solution to our MSP stack designed to deliver even more reliability, security, and value for your business.

Dark Web Monitoring
Our 24/7 Dark Web Monitoring solution provides critical alerts for business domain and employee credentials. The earlier you know about these compromises, the sooner you can reset passwords and resolve these security gaps.
We leverage the power of both advanced technology intelligence and human analysts to proactively search for and analyze compromises and exposed login credentials that can make your business a hot target for cybercriminals.
Dark web monitoring scans known dark web forums, marketplaces, paste sites, and breach databases for:
- Compromised email addresses
- Usernames and passwords
- Employee credentials
- Company domains
- Personally identifiable information (PII)
When a match is found, we're alerted immediately.
Stolen credentials are often sold or shared on the dark web and then used for:
- Account takeovers
- Business email compromise (BEC)
- Ransomware attacks
- Phishing and impersonation
Dark web monitoring gives you early warning, so you can act before damage is done.
Saas Alerts
Modern businesses rely heavily on SaaS platforms like Microsoft 365, Google Workspace, CRMs, and accounting systems. While these tools improve productivity, they also create new security and availability risks. SaaS alerts provide real-time visibility into what’s happening inside those platforms—so issues are caught early, not after damage is done.
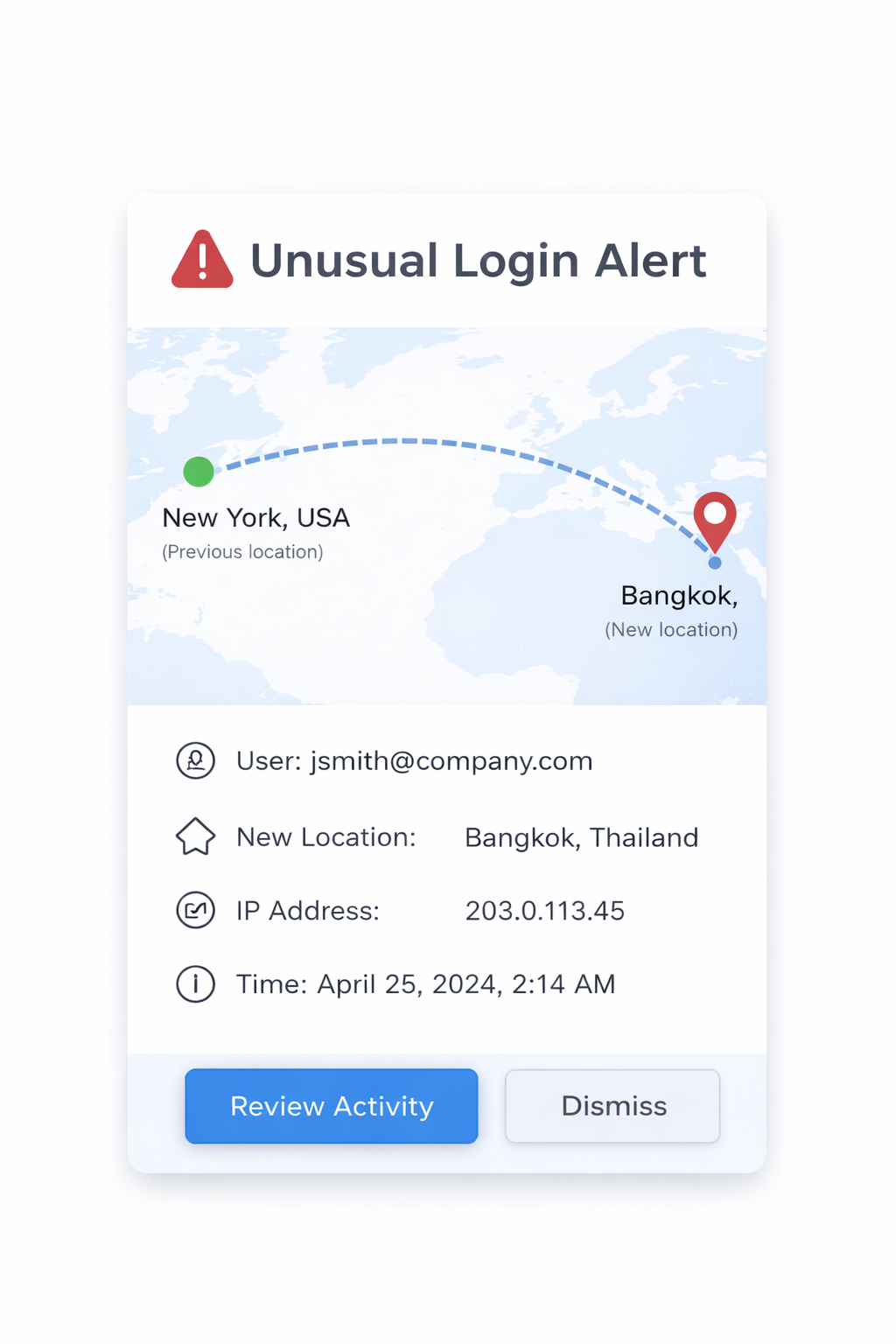
Threats
-------------------------------------------------------------
SaaS alerts notify us immediately when suspicious activity occurs, such as:
- Unusual login locations
- Multiple failed sign-in attempts
- New devices accessing accounts
- Changes to security settings or permissions
This allows fast response to prevent account compromise, data loss, or ransomware attacks.
Response
------------------------------------------------------------
Instead of discovering problems after users are impacted, SaaS alerts:
- Identify service disruptions early
- Flag syncing or backup failures
- Detect deleted or altered data
The result is faster resolution and less downtime for your business.


Inky Email Monitoring
Email threats continue to be one of the leading causes of security incidents. That’s why we’ve added Inky Email Monitoring—an advanced layer of protection that detects and stops phishing attacks before they reach your inbox.
Inky uses AI and behavioral analysis to detect:
- Phishing and spear-phishing emails
- Business email compromise (BEC)
- Impersonation and look-alike domains
- Malicious links and attachments
Unlike basic filters, Inky analyzes intent and context, not just known signatures.
Even trained employees can be tricked by well-crafted emails. Inky adds a clear warning banner to suspicious messages, helping users make safer decisions and reducing the risk of accidental clicks.
Inky continuously monitors inboxes and:
- Alerts us to active threats
- Allows rapid investigation and remediation
- Removes malicious emails already delivered
-
This means threats can be stopped even after they bypass other defenses.

BullPhish
BullPhish strengthens your security by educating employees, reducing phishing risk, and creating a more resilient organization—making it a smart addition to any modern IT security stack.
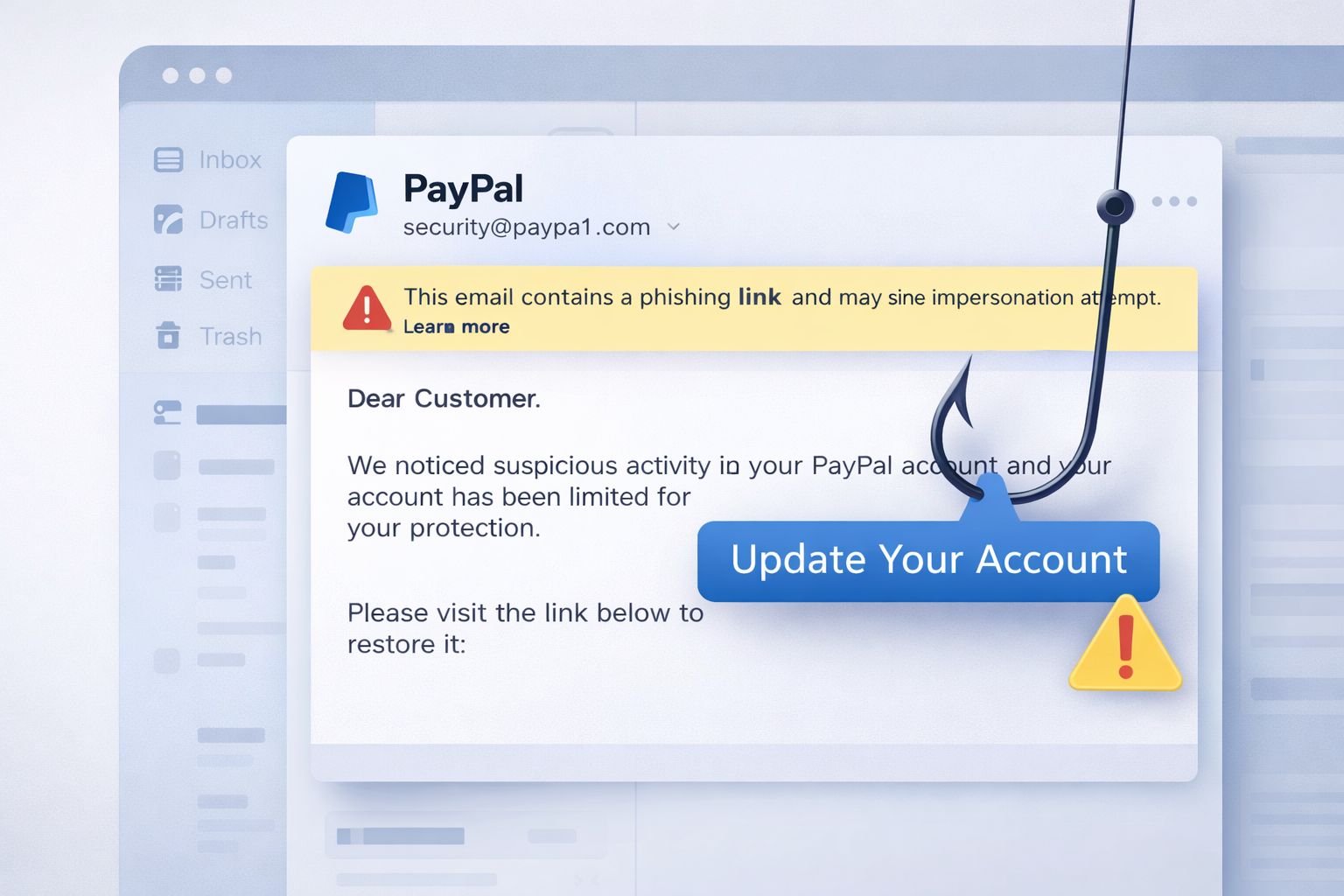
BullPhish trains employees to recognize and avoid:
- Phishing and spear-phishing emails
- Business email compromise (BEC) scams
- Credential-harvesting attacks
- Malicious links and attachments
-
By improving awareness, employees become a strong line of defense, not a liability.
Unlike one-time training sessions, BullPhish delivers:
- Automated phishing simulations
- Continuous micro-training
- Realistic attack scenarios employees actually see
This keeps security awareness fresh and effective.
When a user falls for a simulated attack, BullPhish:
- Instantly delivers targeted training
- Reinforces what went wrong and how to avoid it next time
This creates improvement without blame or disruption.

This new addition to our IT stack is part of our ongoing commitment to proactively protect, support, and strengthen your technology environment. As threats evolve and businesses rely more on cloud services, we continue to invest in tools that deliver greater security, visibility, and peace of mind—so you can stay focused on running your business.
-Your Team at The Link Layers